What is a crypto honeypot and why is it used?
Modern blockchains like Ethereum allow for decentralized smart contract execution. Smart contracts are growing increasingly popular and valuable, enticing attackers. Hackers have recently targeted several smart contracts.
However, a new trend appears to be emerging: attackers are becoming more proactive rather than reactive in their approach. Instead, they send out contracts that appear vulnerable but contain hidden traps. Honeypots are a special type of contract. A honeypot crypto trap, then?
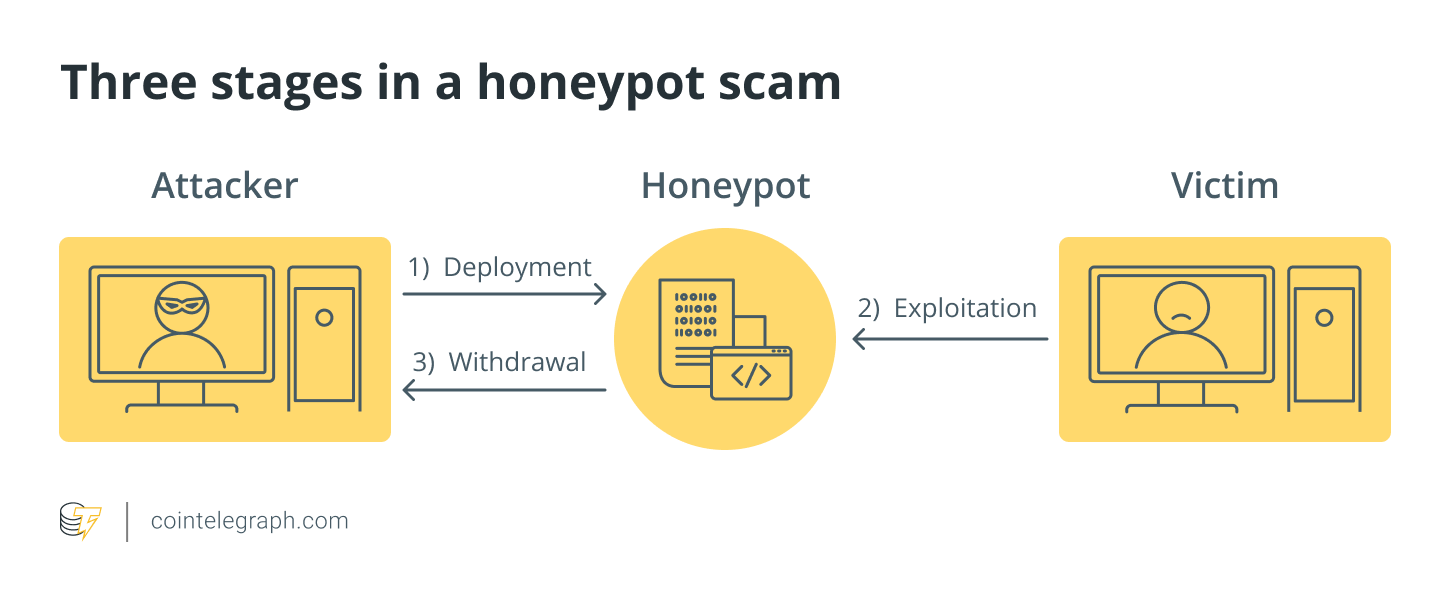
As it turns out, honeypots are smart contracts with a design flaw that allows an arbitrary user to drain Ether (Ethereum’s native currency) from the contract by sending it a certain amount beforehand. When the user attempts to exploit this apparent defect, a second unknown trapdoor opens, halting the ether draining. Que fait un honeypot?
The goal is for the user to overlook any indicators that the contract contains a second vulnerability. Like other forms of deception, honeypot assaults work because individuals are readily fooled. As a result, people’s avarice and assumptions can sometimes obscure risk. So, are honeypots illegal?
How does a honeypot scam work?
In crypto cyber attacks such as honeypots, the user’s money is imprisoned, and only the author of the honeypot (attacker) has the ability to recover it.
Typically, a honeypot operates in three stages:
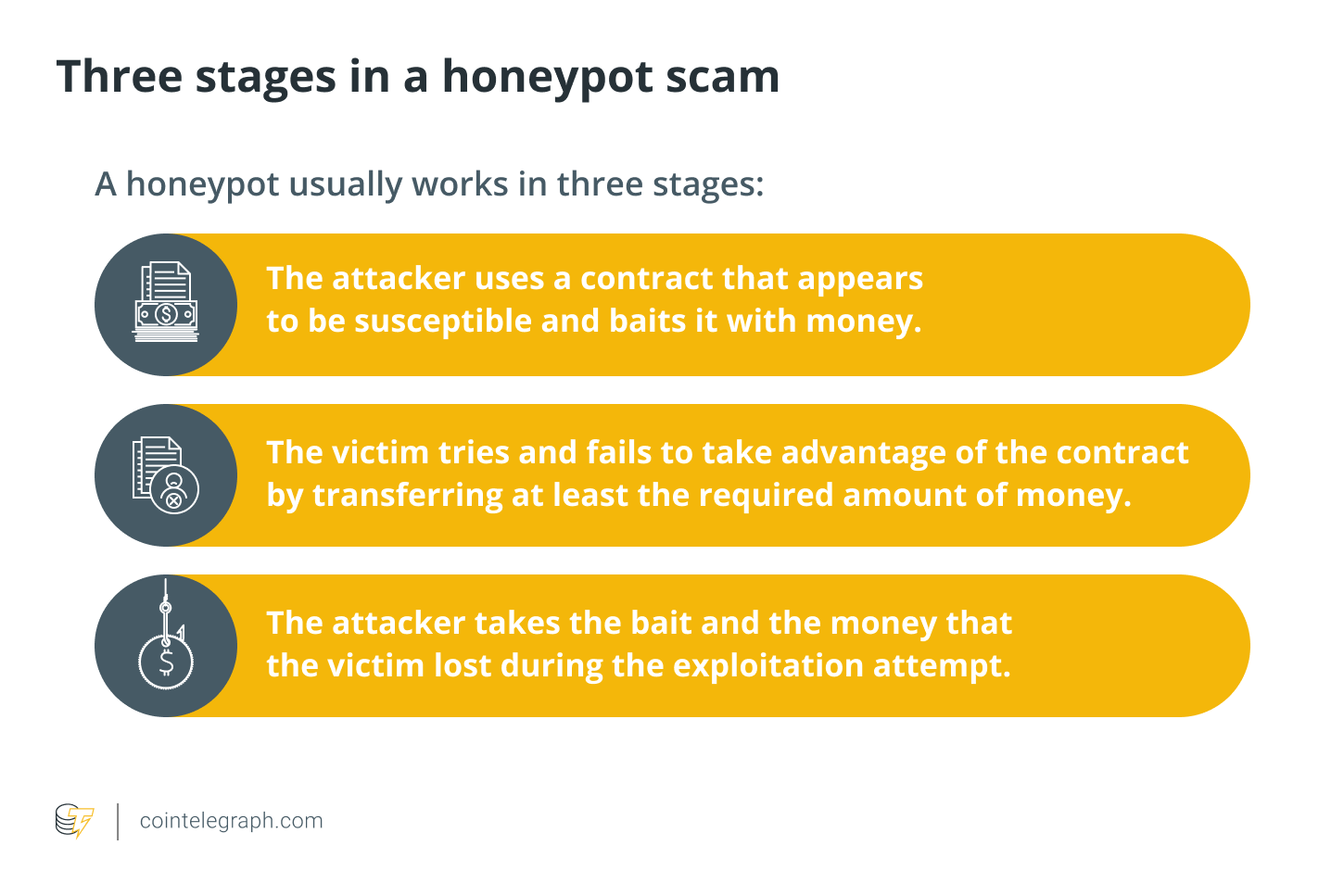
An attacker does not require any special abilities to set up honeypots with Ethereum smart contracts. In reality, an attacker possesses the same abilities as a regular Ethereum user. They simply require the funds to set up and bait the smart contract. In general, a honeypot operation consists of a computer, applications, and data that simulate the behavior of a genuine system that may be attractive to attackers, such as Internet of Things devices, a financial system, or a public utility or transit network.
Despite its appearance, it is separated and supervised. A honeypot’s communication with legitimate users is seen as hostile. Many networks have a demilitarized zone with honeypots (DMZ). This method keeps it isolated from the leading production network. This reduces the risk of a compromised main network by monitoring a honeypot in a network’s demilitarized zone (DMZ).
Honeypots can be installed outside the external firewall, facing the internet, to detect intrusion attempts. The honeypot’s location relies on its complexity, the traffic it seeks to attract, and its proximity to vital business resources. The environment will always be segregated from the production environment.
By diverting attackers‘ attention from real-world assets, honeypot activity logs and displays the degree and types of threats that a network infrastructure faces. Honeypots can be hijacked by cybercriminals and used against their owners. Honeypots have also been used to gather information on researchers or organizations, or to spread misinformation.
Virtual machines regularly host honeypots. For example, a malware-infected honeypot can be quickly restored. Examples of honeynets and honey farms include a network of honeypots and analysis tools.
Both open source and commercial tools can help deploy and manage honeypots. There are single and combination honeypot systems promoted as deception technology. GitHub has honeypot software that can help newbies learn how to use honeypots.
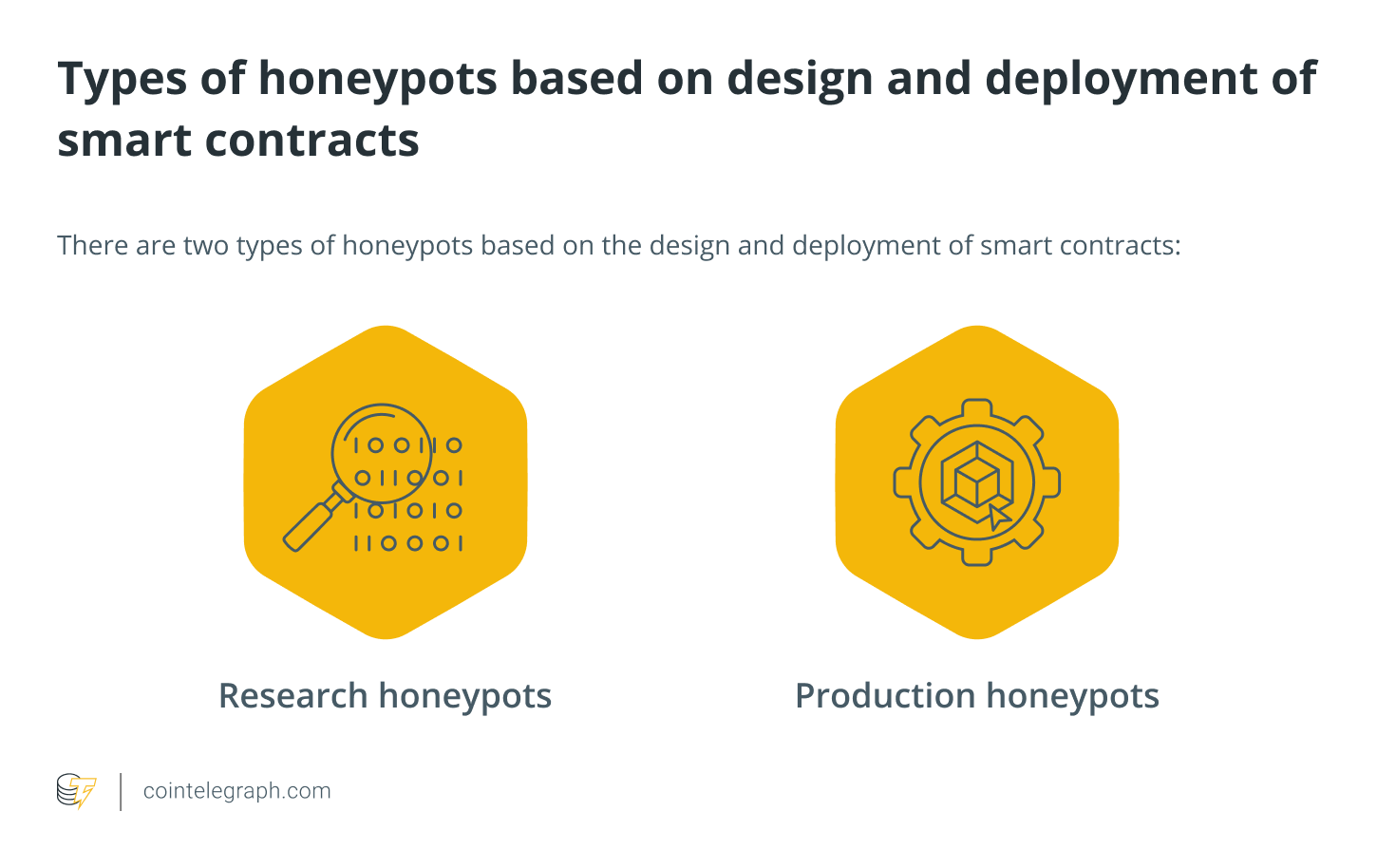
Types of honeypots
Honeypots based on the design and implementation of smart contracts can be divided into two categories: research honeypots and production honeypots.
For scientific research purposes, honeypots are used to gather information about attacks and to examine hostile behavior in the wild.
They gather information on attacker tendencies, vulnerabilities, and malware strains that are currently being targeted by looking at both your environment and the outside world. This data can assist you in making decisions about preventative defenses, patch priorities, and future investments.
Production honeypots, on the other hand, are designed to detect active network penetration and deceive the attacker. Honeypots provide additional monitoring opportunities and fill common detection gaps associated with identifying network scans and lateral movement; thus, data collection remains a top priority.
Production honeypots run services that would normally run alongside the rest of your production servers in your environment. Honeypots for research are more complex and store a wider range of data types than honeypots for production.
There are also several tiers within production and research honeypots, depending on the level of sophistication required by your company:
- High-interaction honeypot: This is comparable to a pure honeypot in that it operates a large number of services, but it is less sophisticated and holds less data. Although high-interaction honeypots are not intended to replicate full-scale production systems, they run (or appear to run) all of the services commonly associated with production systems, including functioning operating systems.
Using this honeypot form, the deploying organization can observe adversary tactics. They require a lot of resources and maintenance, but the results might be worth it. 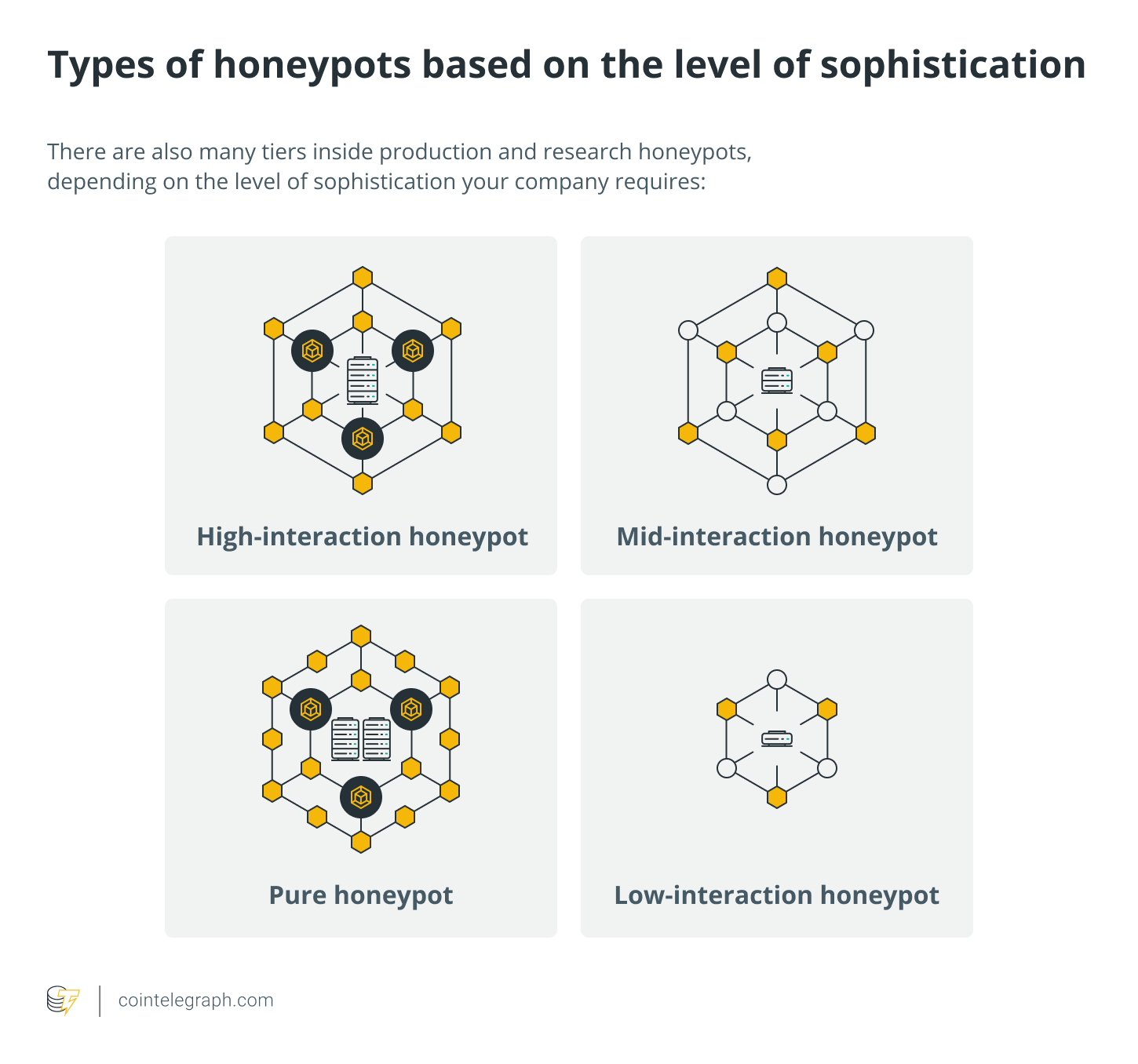
- Mid-interaction honeypot: These imitate characteristics of the application layer but lack their operating system. They try to interfere or perplex attackers so that businesses have more time to figure out how to respond appropriately to an attack.
- Low-interaction honeypot: This is the most popular honeypot used in a production environment. Low-interaction honeypots run a few services and are primarily used as an early warning detection tool. Many security teams install many honeypots across different segments of their network because they are simple to set up and maintain.
- Pure honeypot: This large-scale, production-like system runs on multiple servers. It is full of sensors and includes „confidential“ data and user information. The information they provide is invaluable, even though it can be complex and challenging to manage.
Several honeypot technologies
The following are some of the honeypot technologies in use:
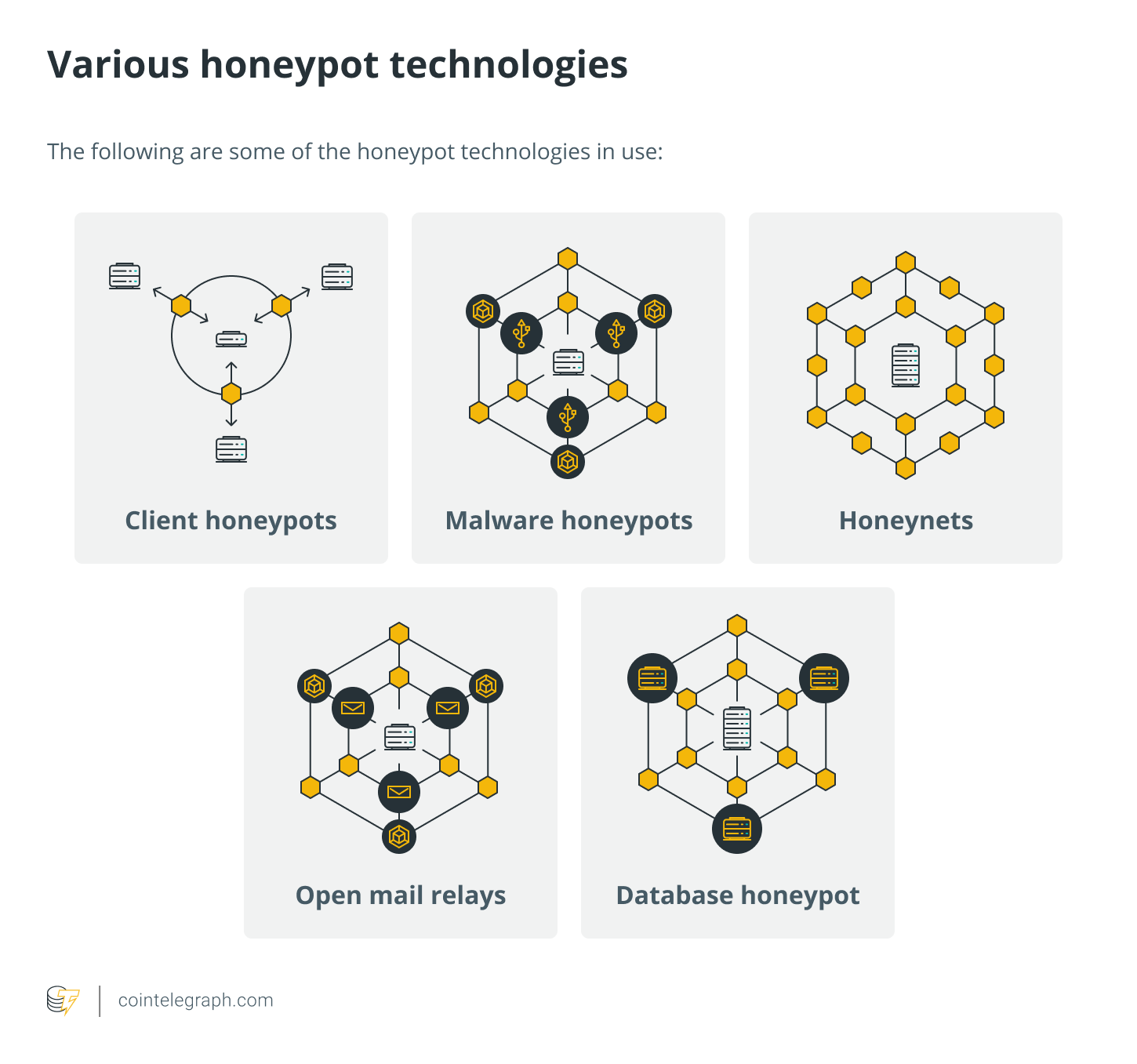
- Client honeypots: The majority of honeypots are servers that are listening for connections. Client honeypots actively search out malicious servers that target clients, and they keep an eye on the honeypot for any suspicious or unexpected changes. These systems are usually virtualized and have a containment plan in place to keep the research team safe.
- Malware honeypots: These identify malware by using established replication and attack channels. Honeypots (such as Ghost) have been designed to look like USB storage devices. For example, if a machine becomes infected with malware that spreads by USB, the honeypot will deceive the malware into infecting the simulated device.
- Honeynets: A honeynet is a network of several honeypots rather than a single system. Honeynets are designed to follow an attacker’s actions and motives while containing all inbound and outbound communication.
- Open mail relays and open proxies are simulated using spam honeypots. Spammers will first send themselves an email to test the available mail relay. If they are successful, they will send out a tremendous amount of spam. This form of honeypot can detect and recognize the test and successfully block the massive amount of spam that follows.
- Database honeypot: Because structured query language injections can often go undetected by firewalls, some organizations will deploy a database firewall to build decoy databases and give honeypot support.
How to spot a crypto honeypot?
Examining the trading history can help spot honeypot crypto scam. A cryptocurrency should allow you to buy and sell it at will. In a honeypot fraud, the coin will be widely purchased, but difficult to sell. This means it’s a fake coin to avoid.
Moreover, depending on contract transaction behavior, data science may characterize contracts as honeypots or not.
Where can honeypots arise in Ethereum smart contracts?
Honeypots might appear in three different areas of Ethereum smart contracts implementation. These are the three levels:
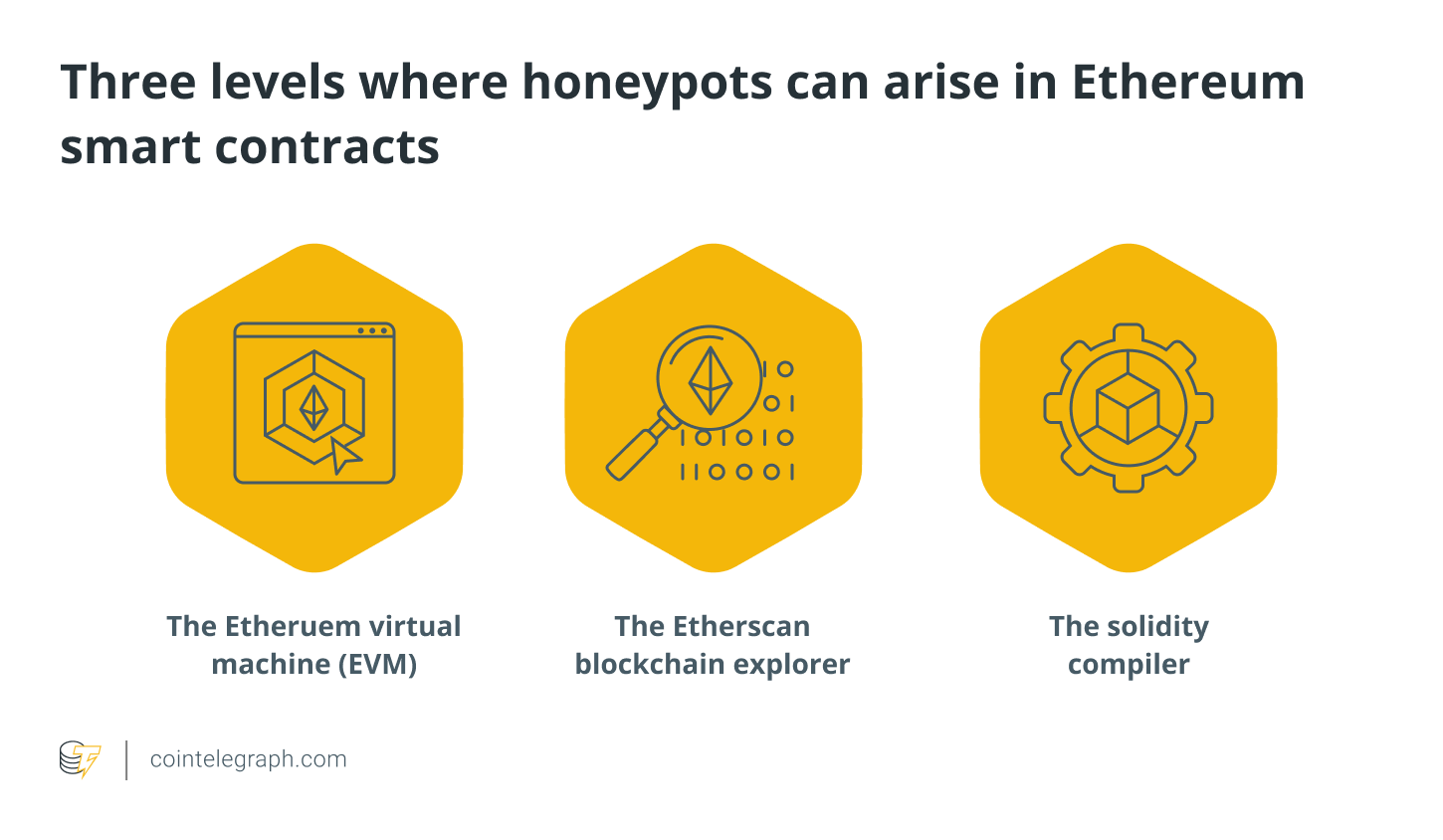
- The Etheruem virtual machine (EVM)- Although the EVM follows a well-established set of standards and rules, smart contract writers can present their code in ways that are misleading or unclear at first glance. These tactics might be costly for the unsuspecting hacker.
- The solidity compiler-The compiler is the second area where smart contract developers may capitalize. While certain compiler-level bugs are well-documented, others may not be. These honeypots can be difficult to discover unless the contract has been tested under real-world settings.
- The Etherscan blockchain explorer-The third sort of honeypot is based on the fact that the data presented on blockchain explorers is incomplete. While many people implicitly believe Etherscan’s data, it doesn’t necessarily show the whole picture. On the other hand, wily smart contract developers can take advantage of some of the explorer’s quirks.
How to protect against honeypot contract scams?
This section discusses how to prevent falling victim to honeypot frauds. There are tools available to aid you in identifying red flags and staying away from these currencies. For example, use Etherscan if the coin you’re considering purchasing is on the Ethereum network, or BscScan if the coin is on the Binance Smart Chain.
Determine the Token ID for your coin and enter it on the proper page. On the following screen, click „Token Tracker.“ There will now be a tab named „Holders.“ There, you may view all of the wallets that store tokens and liquidity pools. Regrettably, there are countless possible combinations of items to consider. The following are some red signals that you should be aware of in order to protect yourself against honeypot cryptocurrency scams:
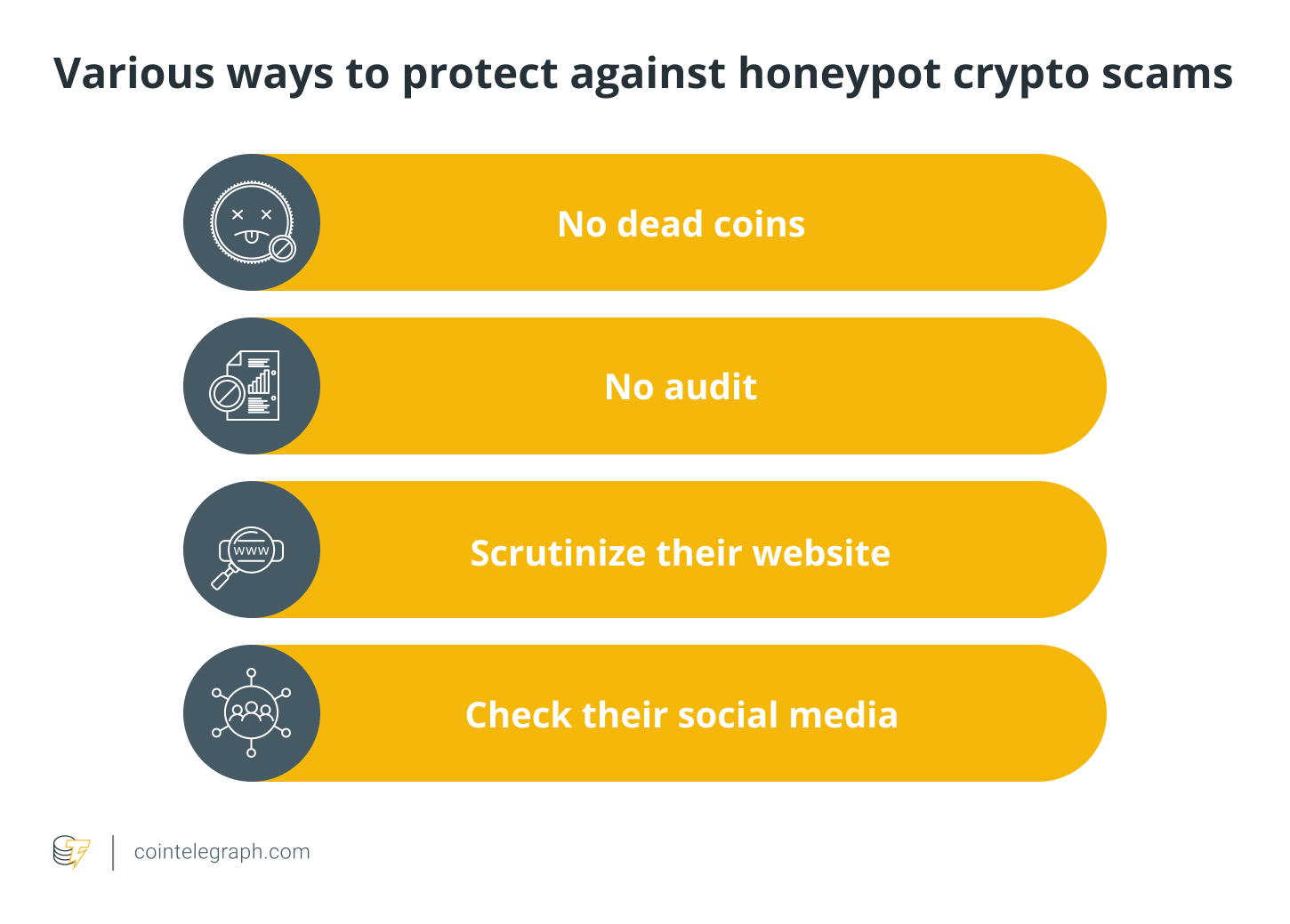
- No dead coins: If more than 50% of coins are in a dead wallet, a project is relatively protected from rug pulls (but not a honeypot) (usually identified as 0x000000000000000000000000000000000000dead). If less than half of the coins are dead or none are dead, be cautious.
- No audit: The chances of a honeypot are nearly always eliminated if a trustworthy company audits them.
- Large wallets holders: Avoid cryptocurrencies that have only one or a few wallets.
- Scrutinize their website: This should be pretty straightforward; but, if the website appears rushed and the development is poor, this is a warning sign! One trick is to go to whois.domaintools.com and type in the domain name to see when it was registered for a website. You might be quite sure it’s a fraud if the domain was registered within 24 hours or less of the project’s start.
- Check their social media: Scam projects usually feature stolen and low-quality photos, grammatical problems and unappealing „spammy messages“ (such as „drop your ETH address below!“), no links to relevant project information and so on.
Token Sniffer is another fantastic tool for identifying honeypot cryptocurrency. Enter the Token ID in the top right corner to find the „Automated Contract Audit“ findings. Remain away from the project if any alarms are received. Due to the widespread use of contract templates in recent years, the „No prior similar token contracts“ indicator may be a false positive.
If your coin is listed on the Binance Smart Chain, navigate to PooCoin and re-enter the Token ID. Keep an eye on the charts. Avoid buying if no wallets are selling or if only one or two wallets are selling your preferred coin. Almost certainly, it is a honeypot. If a large number of wallets are selling the desired coin, it is not a honeypot. Finally, you should undertake extensive study before investing your hard-earned money in cryptocurrency.
How is a honeypot different from a honeynet?
A honeynet consists of two or more honeypots. A connected honeypot network can be useful. An invasion can be tracked as it moves between network nodes and interacts with multiple sites at once.
The purpose is to convince hackers that they have successfully penetrated the network, thus increasing the realism of the setup. Deception technology refers to advanced honeypots and honeynets that include next-generation firewalls, intrusion detection systems, and secure web gateways. Intrusion detection systems (IDS) monitor a network for malicious activities or policy violations. Automated deception technology allows a honeypot to reply in real-time to potential attackers.
Honeypots can help businesses stay up with the ever-changing cyber threat landscape. Honeypots provide critical information and may be the greatest way to catch an attacker in the act, even if it is hard to predict and prevent every attack. They’re also a useful resource for cybersecurity experts.
What are the pros and cons of honeypots?
Analysts can use honeypots to obtain data from real assaults and other criminal activity. Less false positives. The usage of a honeypot reduces the frequency of false positives because legitimate users have no reason to contact the honeypot.
Aside from that, honeypots are worth investing in because they only engage with damaging acts and do not process huge volumes of network data in search of assaults. Encryption or not, honeypots can detect nefarious activity.
While honeypots have numerous benefits, they also have many downsides and risks. For example, honeypots only collect data during an attack. No efforts to access the honeypot have resulted in no data to analyse the attack.
Furthermore, a honeypot network only collects harmful traffic when attacked; an attacker will avoid a honeypot network if they know it is one.
Honeypots are easily distinguished from lawful production systems by expert hackers utilizing system fingerprinting techniques.
Despite being isolated from the real network, honeypots eventually connect to enable administrators access to the data they contain. As a result of this, a high-interaction honeypot is considered riskier than a low-interaction honeypot.
Overall, honeypots help researchers identify network security threats, but they should not replace traditional IDS. For example, a poorly configured honeypot may be used to gain access to real-world systems or as a launchpad for attacks on other systems.























